AI Memory-related Business Models and Companies 2025
Business models around "AI Memory" are rapidly emerging and crystallizing into distinct layers.
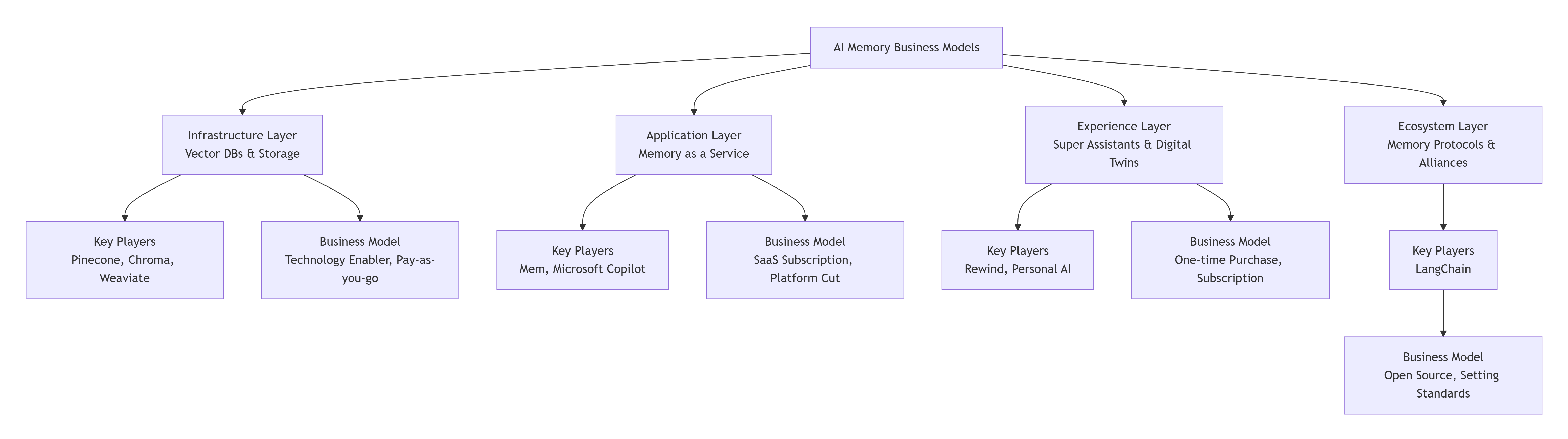
Business models around "AI Memory" are rapidly emerging and crystallizing into distinct layers. The following chart outlines the core business models and key players in this ecosystem:
🔍 Detailed Analysis of Core Business Models
1. Infrastructure Layer: The "Warehouse & Logistics" of Memory
This is the most established and direct business model, providing the underlying technical backbone for all applications that require memory.
Business Model: B2B Technology Enabler. Offering database or cloud services charged based on storage capacity, query volume, etc. (Pay-as-you-go).
Key Players:
Pinecone: A vector database designed specifically for AI applications, allowing developers to easily store and retrieve vast amounts of "memory" embedding vectors.
Chroma: An open-source vector database that lowers the barrier to entry for developers.
Weaviate: An open-source vector search engine that also functions as a database.
Outlook: This is the "pick-and-shovel seller" in the AI gold rush. As long as AI applications need long-term memory, they will rely on these services. The market is vast, but competition is intensifying.
2. Application Layer: Memory as a Service (MaaS)
This is the direct embodiment of the SaaS memory system you mentioned and a very active area for startups.
Business Model: SaaS Subscription. Users or developers pay to subscribe to a memory system that can be used across different platforms and applications with the same memory library.
Key Players:
Mem.ai: It positions itself as a "workplace that centers around you," connecting your calendar, email, documents, etc., automatically extracting key information to form memories and proactively providing it when needed. It sells a cross-platform, personal memory brain.
Microsoft Copilot (and its plugin ecosystem): Copilot is evolving into a unified memory for your work life. With your permission, it can access your emails, OneDrive, and Teams chats to provide context-aware assistance in Word, Excel, etc. This can be seen as a "platform-level memory" embedded within the Office ecosystem.
Outlook: Imagine a "1Password for your brain"—a service where you can instantly access your preferences, history, and goals across ChatGPT, Midjourney, your office software, and even your smart home. Its core value lies in breaking down application silos and enabling memory interoperability.
3. Experience Layer: Super AI Assistants & Digital Twins
This model deeply integrates memory functions into a consumer-facing AI product, where memory is the core selling point.
Business Model: B2C Software Subscription or One-time Purchase.
Key Players:
Rewind.ai: It records (with a strong emphasis on local, private processing) everything you see, hear, and say on your device, building a searchable memory. When you interact with an AI, it uses this comprehensive contextual memory to answer questions. It sells "a super-assistant that remembers everything you've seen and heard."
Personal AI: Aims to train an AI that is unique to you using your data. It can mimic your language style and knowledge to help you reply to emails or generate content. It sells "your digital twin," and memory is the foundation of this twin.
Outlook: These products are at the cutting edge, directly touching on the realms of "digital immortality" and "human-machine integration." The market potential is enormous, but it comes with significant privacy and ethical challenges.
4. Ecosystem Layer: Memory Protocols & Alliances
This is the most forward-looking model, aiming to create a "universal standard" for memory to solve cross-platform compatibility.
Business Model: Establishing standards through open-source protocols or industry alliances, profiting from ecosystem influence (e.g., certification, premium enterprise services).
Key Players:
LangChain's "LangChain Memory" module: while a development tool, is attempting to become the de facto standard for developers building memory into Agents. If successful, it would hold significant influence over the ecosystem.
The Possible Future: The emergence of an open standard like an "OpenAI Memory Protocol," allowing users to securely migrate their memories from one service to another. This could lead to services like "memory banks" or "memory vaults."
Outlook: This follows the "winning through standards" path. It is the most difficult route, but success would mean controlling the lifeline of the entire ecosystem.
💡 Ideas for Entrepreneurs and Innovators
Based on the models above, here are some potential directions to explore:
Vertical-Specific Memory Experts: Instead of building general-purpose memory, focus on systems for specific industries like law, healthcare, education, or finance. These systems would be pre-loaded with industry knowledge and learn from the user's proprietary data, becoming an expert assistant for experts.
Memory Privacy & Security Services: As memories become more critical, there will be a demand for "memory banks" or "memory safes." Offer services with end-to-end encryption and zero-knowledge proofs to ensure no one but the user can access the data.
Memory Analytics & Insight Services: Help businesses or individuals analyze their memory data to identify knowledge gaps, efficiency bottlenecks, or innovation opportunities. For example, "Your work memory shows you spend 40% of your time on project management, but 60% of that is ineffective communication. We recommend..."
Challenges and Caveats:
Data Privacy & Security: This is the biggest challenge and potentially the greatest commercial moat. Gaining user trust is paramount.
Data Standardization: Memory data generated by different applications comes in various formats, making integration difficult.
User Adoption: Will users be willing to entrust their digital lives to a "memory system"?
Conclusion:
The "AI Memory" space is undoubtedly a golden frontier brimming with commercial potential. It is at an inflection point, transitioning from building infrastructure to launching application ecosystems. Whether you focus on core technology, cross-platform SaaS, or vertical applications, significant opportunities exist. The key is to find a precise entry point and build a robust trust framework that addresses the user's core concerns about privacy and security.
This article was written by the author with the assistance of artificial intelligence (such as outlining, draft generation, and improving readability), and the final content was fully fact-checked and reviewed by the author.